✉️ In Today’s Newsletter
In todays deep dive, I break down everything about Why Compliance is Important In DevOps, Key Compliance Standards, Compliance as Code ad more..
Also we will look at xDS, HBONE Protocols & Remote Jobs
🧰 Featured - 67% off OpenClaw VPS hosting

Run your own AI assistant with self-hosted OpenClaw on Hostinger VPS for full control, persistent availability, and 24/7 uptime.
According to Gartner, 70% of enterprises in regulated verticals will have integrated Compliance as Code into their DevOps toolchains by 2026.
One of the most common failures I see in production environments is the huge gap between organizational compliance rules and the CI/CD pipelines engineers actually build.
In theory, governance is strict. In practice, engineers bypass these rules every day.
I learned this early in my career. My first major automation project involved running HIPAA compliance checks on Linux servers.
Before going deeper, let’s first understand what compliance means in IT.
What is Compliance?
Every organization has rules designed to keep systems safe, protect user data, and meet legal requirements.
These rules can come from Government regulations, Industry standards or Internal company policies.
Simply put, compliance set of rules and processes that ensures the data is protected, systems are secure, and the organization is audit-ready to avoid legal and financial troubles.
In IT terms, these rules translate into technical implementation. For example, if compliance says “Protect data from unauthorized access”, in IT this becomes,
Firewall rules
Network segmentation
Encrypt data at rest and in transit.
RBAC (Role-Based Access Control)
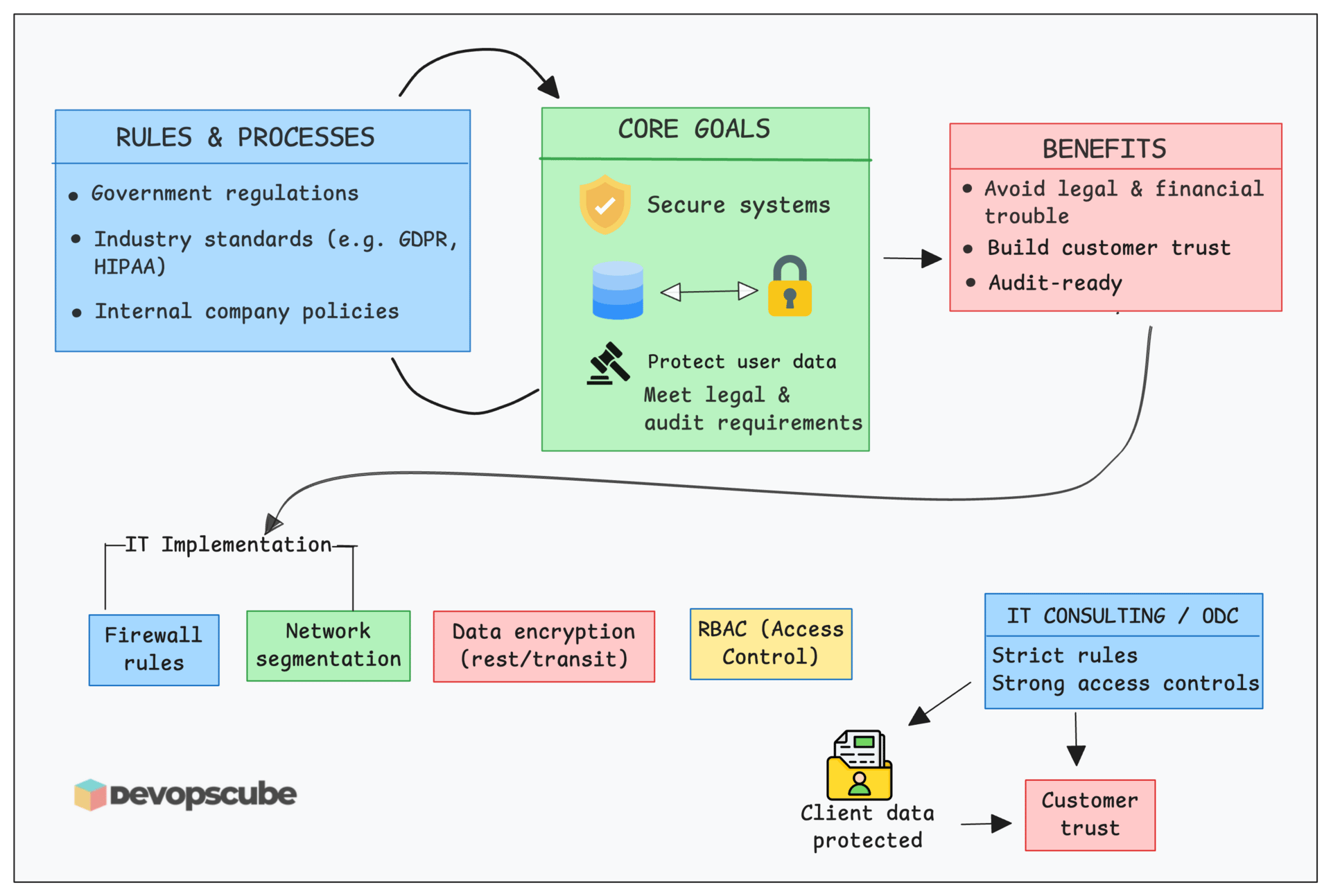
In IT consulting, following compliance standards helps build customer trust by showing that their data is handled safely and responsibly.
That is why companies set up ODCs (Offshore Development Centers) with strict rules, access controls, and security regulations. These controls ensure that client data stays protected and is not misused.
Compliance = What you must follow and prove during audits.
Key Compliance Standards
The following are some of the key compliance standard examples.
GDPR (General Data Protection Regulation) - To protect personal data and the privacy of European citizens
HIPAA (Health Insurance Portability and Accountability Act) - To protect the patients’ health information in the U.S
PCI DSS (Payment Card Industry Data Security Standard) - To secure the credit/debit card information.
SOC 2 (System and Organization Controls 2) - Focused on managing customer data based on five trust principles: security, availability, processing integrity, confidentiality, and privacy. Common in SaaS and B2B environments.
Why Compliance is Important In DevOps?
As I explained earlier, compliance rules often translate directly into IT implementations. In that context, DevOps engineers play an important role in designing and setting up the infrastructure and applications.
Take PCI-DSS as an example. If you are working on applications that handle payment data, your setup needs to follow stricter security practices. That means:
Enforcing tighter firewall rules
Isolating workloads with proper network segmentation
Managing access controls and audit logging more aggressively.
When compliance is ignored, minor configuration errors can escalate into serious security breaches, data leaks, and severe legal penalties.
Lets look at a few real examples of compliance failures and the incidents that followed.
Most of these failures come from weak IT controls or missing processes.
In 2024, the Hospital for Special Surgery (NYC) paid $4.75 million for exposing patient records through an unsecured email server.
In 2019, Capital One paid an $80 million fine for a cloud misconfiguration affecting 100 million customers, plus $190 million in class-action settlements.
In 2023, Meta paid a €1.2 billion GDPR fine, the largest in history, for transferring EU user data to U.S. servers.
This is why, in enterprise environments, even small changes like firewall updates or access to external resources go through a long approval process. It is part of managing risk and ensuring compliance.
Compliance as Code
Compliance as Code means implementing compliance requirements as automated checks that run continuously in CI/CD and infrastructure workflows.

Traditionally, compliance was checked after deployment (audits)
Now it becomes part of the DevSecOps approach and helps us “shift left” by catching compliance and security issues early in development rather than after deployment.
For example,
“All S3 buckets must be encrypted.”
“No Kubernetes cluster should allow anonymous access.”
“All logs must be stored for 90 days.”
So how do we enforce it?
This is where Compliance as Code comes in. It falls under the DevSecOps umbrella.
Lets understand that in the next section.
Implementing Compliance as Code
You cannot achieve continuous compliance with manual checklists. You need to automate the guardrails.
Policy as Code is the mechanism used to enforce Compliance as Code in DevOps pipelines.
Write compliance rules as code using Open Policy Agent (OPA) / Kyverno, etc. For example, deny any deployment to production namespace if the container runs as root" (Maps to SOC 2 / ISO least privilege)
The following image illustrates how Policy as Code is used to enforce Compliance as Code in an IaC workflow.

Here is how it works
Start by defining clear and specific policies for your infrastructure. These policies might include security standards, resource allocation limits, naming conventions, etc.
Use Checkov for prebuilt compliance checks (PCI, HIPAA, CIS). Use OPA / Kyverno / Sentinel for custom compliance rules and guardrails.
Establish a PR-based workflow for IaC development. Any changes to the infrastructure should be made via a branch, followed by a PR to merge the changes into the main branch.
When a PR is created or updated, the policy as code tool automatically checks the proposed changes against the defined policies. This is typically done through a Continuous Integration (CI) pipeline using tools like Jenkins, GitHub Actions, GitLab CI/CD, etc.
If the changes pass the policy checks, they move forward to the review stage, where team members can review and discuss them. If the changes fail the checks, the engineer is notified to make the necessary adjustments.
Once the PR is approved and it complies with all policies, it can be merged into the main branch. From there, the changes can be deployed to your infrastructure, often using Continuous Deployment (CD) tools.
Thats a Wrap!
Let’s be honest. Most engineers hate the word compliance.
In many companies, compliance is a boring 50-page PDF stored in some SharePoint folder that nobody reads. So people see it as paperwork instead of something important.
But that's starting to change, thanks to AI. Now, LLMs/Coding agents can accelerate this process significantly.
For example,
From compliance document, "All personally identifiable information (PII) must be encrypted at rest using AES-256 encryption or equivalent."
Prompt to LLM, “"Convert this compliance requirement into an OPA Rego policy that checks AWS S3 bucket configurations."
🧱 HBONE: Istio’s Efficient Network Protocol
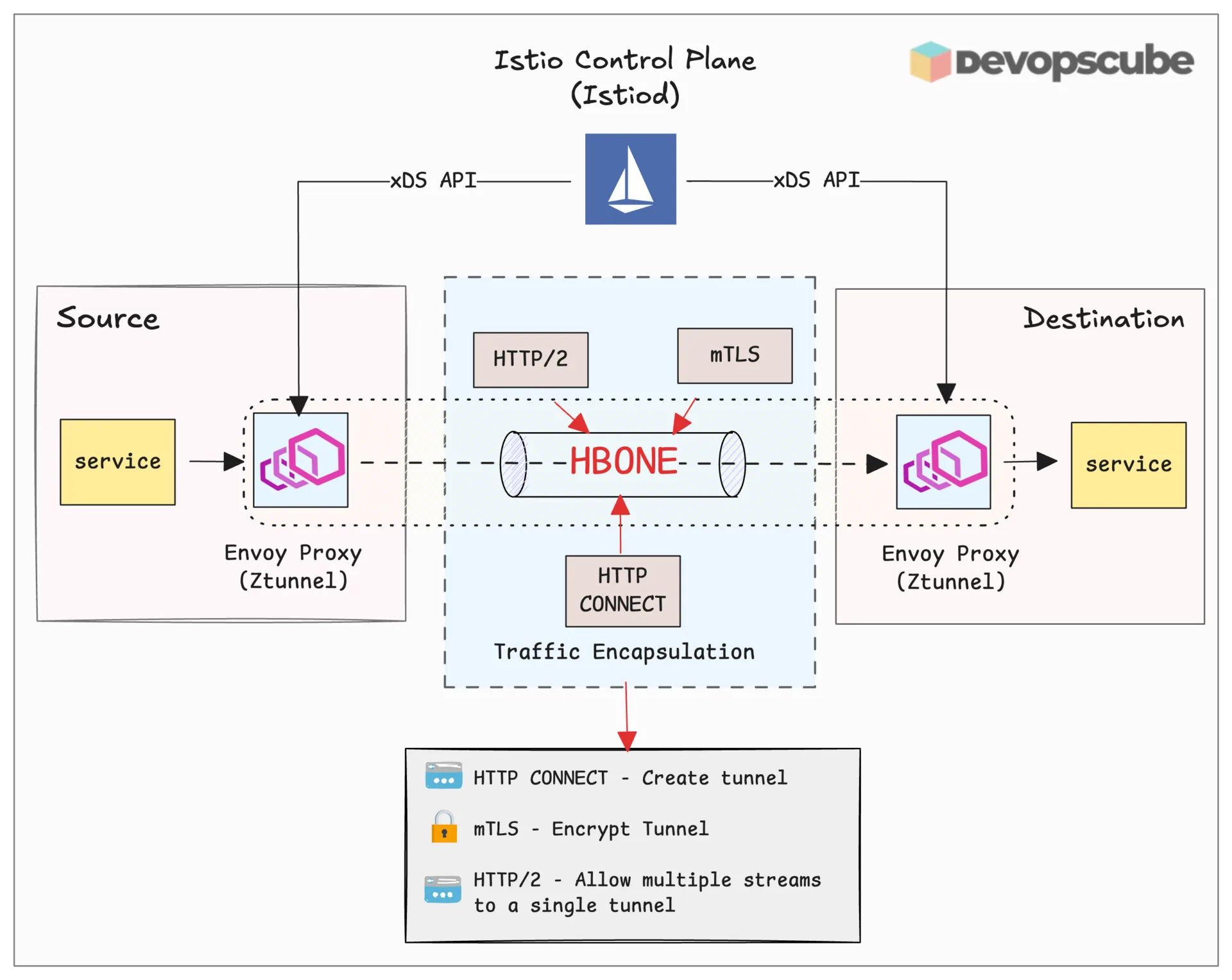
HBONE (HTTP-Based Overlay Network Environment) is a standard way to wrap raw TCP traffic inside an HTTP request.
It is basically how Istio safely moves traffic inside a Kubernetes cluster.
It creates a secure tunnel that carries traffic between service proxies as illustrated in the image below.
🧱 xDS Protocol: The Secret Behind Zero-Downtime Routing

Envoy’s xDS protocol has become the standard way to configure Istio service mesh. It is the protocol that Istio control plane uses to talk to the data plane.
When Istio watches Kubernetes resources like services, routes, or traffic rules, it turns them into Envoy configurations and pushes them to the Envoy proxies using xDS APIs
🧰 Remote Job Opportunities
🤝 Help a Teammate Learn
Found this useful?
Share the subscription link with a colleague or fellow DevOps engineer.

